My OSCP Journey
I obtained the OSCP in November after signing up for Offensive Security's one-year subscription in 2021. I went from basically zero offensive security experience to OSCP in a short time. During that time, I've read countless other peoples' experiences related to their own OSCP journey, which helped me quite a bit. This post is aimed at people who are studying for, or interested in, taking the OSCP.
My background permalink
While I had little offensive security experience before I started my OSCP journey, I have a background in cybersecurity. I started working as a Cloud Security Engineer in 2017, focusing on securing AWS environments. I later moved on to a Security Operations team as a Security Engineer, helping to automate processes like secure AWS account creation and vulnerability management. A couple years ago I moved on to my current role as a Security Engineer, this time within a business-unit that looks at the organization from an adversary perspective. I got some exposure to red teaming (not first hand!) and decided that I wanted to learn more about it. After reading about various ethical hacking type certifications (and being turned off by EC-Council and CEH), I figured I'd jump into the deep end and start with OSCP.
Oh yeah, and somewhere in there I got my degree in cybersecurity from the online school, WGU. While I'm proud to have gotten a degree, especially while working full time, I learned way more during my OSCP studies.
I signed up. Now what? permalink
In late August 2021, I registered for the course. This was before the more recent course changes by OffSec. When I signed up, I received a very long PDF, a link to download some instructional videos, and some instructions on how to set up a Kali VM and connect to the internal portal via VPN. I'll be honest, I was overwhelmed at this point. I started working through the PDF first, going through chapters, trying to take thorough notes and do each of the exercises in the PDF (the bonus points offered by OffSec required a lab report to be written and the results of the chapter exercises to be captured within the report). While I was learning about tools and specific techniques, my approach felt piecemeal; when trying to work against a specific system in the labs, I had no idea where to start, how to enumerate, etc. I wasn't building a methodology (a word that I kept seeing everywhere).
I came across someone who mentioned IppSec's YouTube - I think on the OSCP subreddit (this subreddit and the OffSec Discord were two of my favorite resources). Watching IppSec's videos gave me a better understanding of how to think, what types of command to run, and what types of things to look for. I learned about some common nmap arguments and how to use things like gobuster to enumerate web applications. My methodology was taking some shape. It was still a lot to take in, though. I remember watching his walkthrough of Poison, seeing him use a PHP Filter Wrapper (/browse.php?file=php://filter/convert.base64-encode/resource=index.php) and thinking to myself, "How does he know all this stuff? Do I have to learn PHP too!? I would never have thought to do that." It's daunting to see how much there is to learn and how much learning you have left to do. But it's important to remind yourself that the people who have that knowledge all had to work to get it too. ippsec.rocks is a wonderful site to search through if you're looking for a quick walkthrough on a specific technique.
By this point I'd taken a step back from doing the PEN-200 labs and exercises and shifted towards retired HackTheBox systems where I could find videos and/or walkthroughs. I bought both of Tib3rius's privilege escalation courses on Udemy, which helped a bit, but there was still much I didn't understand. I also purchased the TCM Security Practical Ethical Hacking course, which I began to work through as well.
Life is what happens to you while you're busy making other plans permalink
As it got closer towards the end of 2021, my focus shifted away from studying for the OSCP.
I got married in early December. My wife and I skipped our honeymoon (Delta was rampant and shutdowns were coming back). We hired a realtor and began looking for a house days after our wedding. Our lease was expiring at the end of March, so we had a pretty tight timeline. My weekday evenings went from hacking boxes to surfing Zillow. We spent our weekends with the realtor more often than not. The housing market was going nuts and houses were being sold within days.
On top of all this OffSec announced changes to their course. Active Directory was to take a much larger role, the bonus points format changed. There was a whole new way to interact with exercises and the labs, and I didn't have time to keep up with the changes. So far, I had spent most of my time hacking Linux boxes, so the new emphasis on Windows and AD was intimidating.
Then my uncle Dewey died in February. He was the closest person in my life for as long as I can remember and it was a big loss for me. He taught me so many things, but the one thing he always harped on was that I could do anything I wanted if I worked for it. He would have totally resonated with the mantra: "Try Harder".
My wife and I managed to buy a house, and we moved in late March. It was an enormous relief. But by this point, I'd lost all the momentum I'd built when I started PEN-200. I hadn't studied in months and was immersed in everything that comes with buying your first home.
Resuming the journey permalink
It wasn't until July that I resumed my studies for the OSCP.
My work had hosted a small CTF event. It was the first time I'd met a lot of colleagues in person, including some folks from the red team. It was the first time I'd hacked anything since the previous year. One challenge involved SQL injection vulnerability, I used sqlmap for the first time ( sqlmap is not allowed during the OSCP exam by the way) and got an RCE. Let me just say that popping shells never gets old. Endorphins are a great motivator. I started studying with only 6 or 7 weeks of lab time left.
Taking good notes permalink
I spent a lot of time trying to hack the boxes in the lab and build on my methodology. I use Obsidian for note-taking, and began taking notes and building templates for different tactics.
A screenshot of my Templates folder in Obsidian
I would use templates to create my notes for each of the lab systems I was hacking. My workflow generally followed the pattern:
- Create a new folder in Obsidian for the box, using the IP address as the folder name
- Create a "Remote Enumeration" note for that box, using the Remote Enumeration template
- Create a new folder in my Kali VM, using the same IP address as the folder name. I saved the outputs of my scans, etc. here.
- Start enumerating services on the system, creating additional notes using other templates where applicable
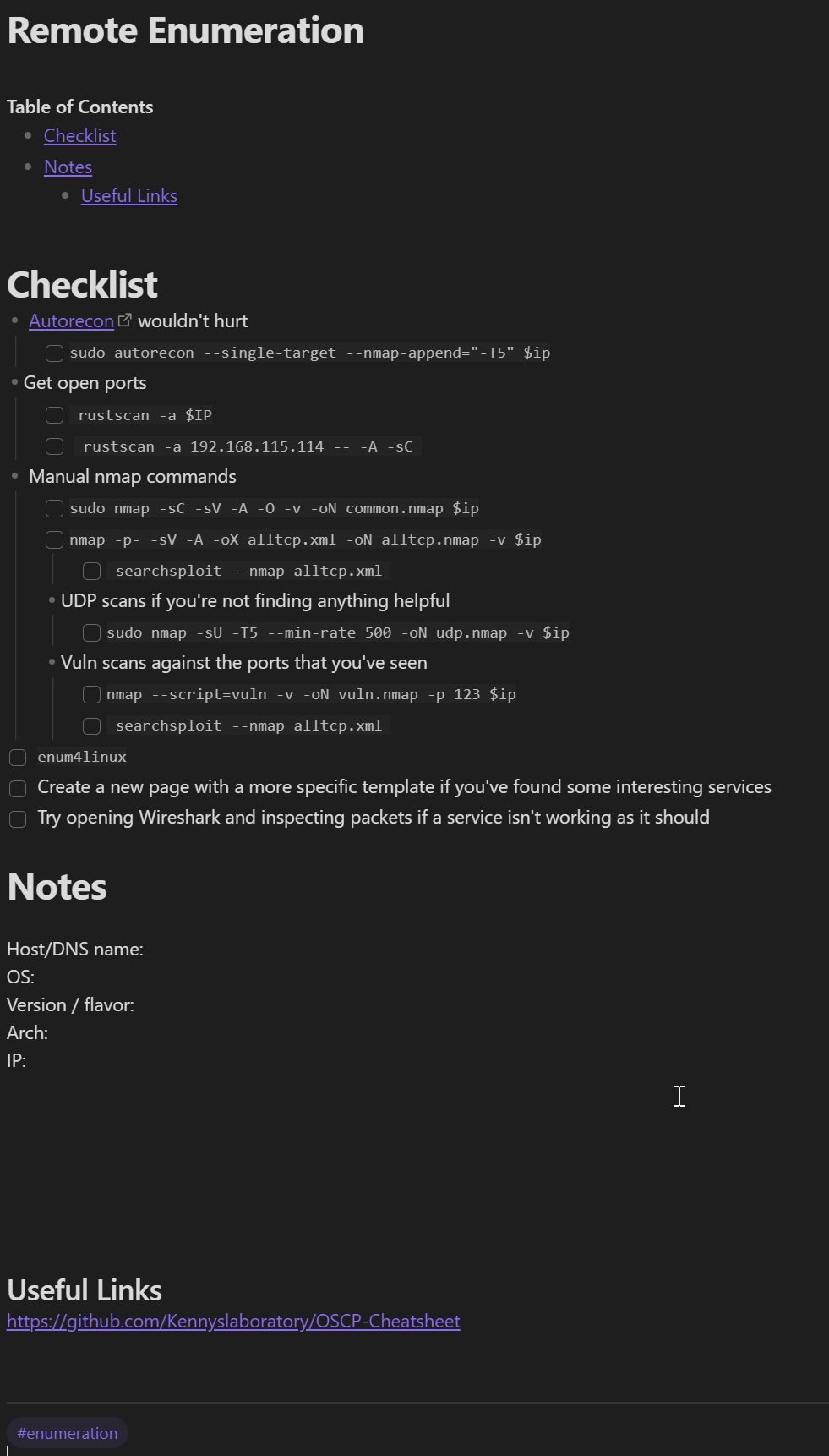
A screenshot of my "Remote Enumeration" template
Every time I encountered something that I felt would improve my notes, I added it to a template. Or I would create a new template for a specific tactic, such as "SMB Enumeration" or "SQL Injection", etc. Having a checklist to go through ensures that you are being systematic with your enumeration. It gives you a framework to use for your labs that you can then carry into the exam setting, so that you're less reliant on remembering what to do next during a stressful exam scenario.
Exercises permalink
I did around 15 lab systems before I switched focus again and started working through the exercises. I will say that the new portal format implemented by OffSec helped keep me motivated, since it's easier to track your progress and visualize what's left to complete. The exercises consist of small tasks that help you practice concepts within a chapter. For each exercise, you spin up a VM and (usually) connect to it via SSH. It can feel a little clunky spinning up a VM and then connecting to it to do an exercise that might take less time to complete than it did to start the VM (though this was infrequent). But overall, the portal format made it a lot easier to get the bonus points. If you have the time, I would recommend doing them.
One thing that I didn't see until after I finished the exercises was a note in the first chapter of the course book that described some additional flags that you should set when SSHing to the exercise machines:
ssh -o "StrictHostKeyChecking=no" -o "UserKnownHostsFile=/dev/null" username@ipAdding those options prevents you from having to clean up your known hosts file between each exercise.
It ended up taking me over a month to complete all the exercises. I was spending around 3 hours per day working on them. I had to pay to extend my lab for another 30 days. Because I was on somewhat of a time crunch, I leaned on the OffSec community for help and hints on some of the harder exercises. I searched and asked a lot of questions in the #pen200-exercises channel in the OffSec discord. The forums are also a good place to look for hints when you're stuck.
For me, the buffer overflow challenges were the hardest exercises by far. Heath Adam's / The Cyber Mentor's Practical Ethical Hacking course (I linked it earlier) helped me a lot. He does a great job of walking you through the steps and explaining things. This Bulb Security article by Georgia Wiedman was very helpful for learning how to deal with bad characters using Mona.py.
Finishing the labs permalink
After completing the exercises, I shifted my attention to the rest of the lab machines. I didn't complete all the lab machines; you only need to complete 30 lab machines to get bonus points. I did 31 just in case. One thing I regret is not doing the additional IT and Dev networks in the lab. It would have been an excellent opportunity to experiment with tools like Chisel - which I still need to get more experience with. Being able to proxy traffic through hosts to different networks is an important skill.
Active Directory permalink
There are two sets of AD machines in the lab that should not be skipped. There aren't a lot of other opportunities available to practice for the AD portion of the exam. I still feel like Active Directory is one of my weaker areas just because I haven't had a lot of practice.
I have a few recommendations for AD:
Get some experience with BloodHound and SharpHound. I used the SharpHound.ps1 collector. Make sure that the versions for BloodHound and SharpHound.ps1 match. You should use one of the packages in the Releases page. When I was first trying it out I downloaded SharpHound.ps1 from the master branch on GitHub and kept getting errors when trying to import my zip file because of incompatibilities.
It's helpful to know your way around PowerView . Here's a cheatsheet that I found useful.
The AD rooms on TryHackMe were pretty helpful ("Attacktive Directory", "Enumerating Active Directory", "Exploiting Active Directory").
Get comfortable with Mimikatz. The
kiwimodule within the Meterpreter payload is also worth experimenting with in the lab environments, just make sure you're careful using it in an exam because you aren't allowed to pivot to another machine using Meterpeter.The impacket scripts. Especially
secretsdump.pyandpsexec.py.CrackMapExec is a really useful tool. I had a hard time getting certain features working, but when it works, it's great. I mostly used it for passing the hash and brute forcing logins. It can be used to get shells as well. Here's a good cheatsheet.
PowerShell Empire is a tool that I wish I had gotten more experience with, as I feel like it would have helped a ton with the AD set. While you're not allowed to use Metasploit to pivot, and can only use it against one host, there aren't any such rules against using Empire as much as you'd like.
Proving Grounds permalink
After finishing the exercises and completing enough lab machines to get the bonus points, I started doing the boxes on Proving Grounds. If you're not familiar, Proving Grounds is OffSec's take on Hack the Box; you can start VM instances on demand for different machines to hack. Each box has two flags, a user flag and an admin flag; you can earn points for each flag you submit. You can also retrieve hints, which cost a certain number of points to reveal. A walkthrough is available for each system, and it explains everything from enumeration to privilege escalation. Proving Grounds has a "Play" tier and a "Practice" tier; Play machines are machines created by the VulnHub community, whereas Practice machines are created by OffSec.
I started out doing Practice machines that were rated as easy by the community and worked my way towards some intermediate machines. I found out about TJ Null's Lists and began doing the Proving Grounds Practice list, focusing on the Windows machines.
In the beginning, I would only look at hints if I'd been stuck for several hours, but most of the time I could get both the flags without looking at any hints. After completing the box, I'd grab the walkthrough and read through it to see if the author did things differently or used different tools/commands. If the walkthrough mentioned anything that I didn't already have in one of my templates or notes, I’d add it somewhere. I'd also copy the walkthrough to my notes for the box, so that I could reference it in the future. Note that you can only view the walkthrough of one machine per day.
The weekend before I took my exam, I was cramming boxes from TJ Null's Practice list. This is when I found out there was a limit for how many walkthroughs you could retrieve in a day (although you can find walkthroughs on blogs). I got in a few of the Linux machines too, since it had been focusing on Windows for weeks at this point. This was invaluable as there were a few scenarios in the TJ Null boxes that were very similar to the exam. The closer I got to the exam, the less strict I was with myself looking up PG Practice walkthroughs. Previously, I'd wait until after I’d been frustrated for a few hours, but now I would start looking after 15-30 minutes of being stuck. Often the technique being used was something I wasn’t familiar with, and I was happy to have "cheated" by looking up a walkthrough. It's hard to look for things that you don't know to look for.
The exam permalink
On the Monday before Thanksgiving, I scheduled the exam. I took the entire week off and used the weekend before as a last-ditch cramming and refresher session. On Sunday, I tried to go a bit easier. I rewatched Tib3rius's Privilege Escalation videos, adding the commands he was using to my cheat sheets if they weren't already there. Because I had more experience using privesc techniques by this point I feel like I absorbed much more on the second watch. I also went through the Active Directory section on Heath Adams's Practical Ethical Hacking course. I tidied my notes up and got ready to go for tomorrow. At this point I felt like there was still a lot left I could study, but there just wasn't enough time. My purchase came with two exam attempts, so I went into the exam thinking of it as a practice test. I scheduled the exam for 10am so that my brain had enough time to wake up. The proctor verification process was straightforward, and I was on my way. I didn't really have a solid plan for which machine to try first, so I just started with the first IP address on the portal. I rooted it in less than two hours! The machine was very similar to one I'd encountered recently, so I knew exactly what to do once I found where the foothold was. I figured it was going to be smooth-sailing from here (I was wrong). After rooting the first machine I took a long walk and ate some lunch, then got back to it.
On the next machine, I spent over an hour looking for a foothold. Many people cautioned about rabbit holes on the exam and there were quite a few that I went down while enumerating. I got a low level shell, but my normal privilege escalation steps weren't turning anything up. I re-ran my tools, kept poking at it from different angles and couldn't figure it out. I ended up moving on to enumeration on a different target and coming back later. Several hours later, I realized I had been overlooking a vulnerability identified by one of the PEAS scripts. This finding was something I'd come across several times before, but it had usually been a false positive. I'd trained my mind to skim past this technique because it wasn't a reliable privilege escalation method, even though it was highlighted on the output of the tool. Learn from my mistake: listen to your privesc tools. I had spent a lot of mental energy by the time I managed to retrieve proof.txt.
I was having a difficult time getting any kind of foothold on the third independent target. This box was a tangled mess of rabbit holes. While there appeared to be some clues, when digging further, I wasn't getting anywhere. I grew frustrated and moved to the AD set, even though I only needed this last independent target to have enough points to pass (including bonus points). I found a foothold and then escalate to retrieve proof.txt but by this point it was 2AM and I was drained. Just the thought of moving laterally and rooting another two boxes hurt my brain. It didn’t feel like I was going to pass this attempt. I figured it was a good time to get some sleep, and crawled into bed and set an alarm for 3 hours. When I woke up, I started enumerating the last individual target again. I can't remember if I had reverted the box before going to sleep, but I seemed to get further with the hints that I tried to chase down earlier. Even though I'd reverted the box twice the previous day, now the service was working like I expected it to. After getting a foothold on the box, I didn't waste any time getting a Meterpreter shell up. I had been keeping Meterpreter in my back pocket, waiting for the right time, and this was it. It didn’t take long to get root. I still had a few hours left, but instead of going after the rest of the AD set I reverted each box and went through each one again, taking good notes and grabbing screenshots of each command. I made some minor changes to my approach the second time around, trying to keep things as simple as possible for the report (for example, using Netcat instead of Socat or using a regular shell instead of a Meterpreter shell). “Keep It Simple Stupid” seemed like the best approach, as I'd have a lower probability of screwing up my instructions and whoever had to follow them would have an easier time as well.
Another recommendation I would make is to count the proof files you've submitted on the OffSec exam portal before ending the exam. I had a mild panic attack after ending the exam because I thought I might have forgotten to submit something (by then it would have been too late).
Writing the report was straightforward. Having taken the time to revert the boxes and go through them again was an enormous help; I could reference a linear page of notes, walking through each step in order instead of having to follow the frenzied train of thought in my initial notes.
It’s over permalink
It took less than 24 hours for my results to come in. I had officially passed! It was a surreal feeling; I had been working so hard to study for this test and suddenly it was over.
While I’m obviously glad to have passed, I’m a little sad that the journey is over. I definitely learned a lot, but I still very much feel like a beginner in the offensive security space. Not entirely sure what’s next for me, but I’m ready for a new challenge.
TLDR permalink
I wish I had some distilled-nugget of information I could that I could pass along. I guess if I had to give a few pieces of advice, they would be:
- Be patient with yourself. There is a ton of material that is covered in this course. Life happens. Sometimes you need to focus on more important things. It's okay. Just get back to it when you can.
- Take good notes. Find a system that works for you. People say that you should make your own notes, not just reference other people's cheat sheets. I agree with them.
- If you're starting from ground zero, it's a good idea to watch other people (like IppSec) do walkthroughs so you can get an idea of their approach.
- If you're stuck on a lab machine or a specific box, look for help (OffSec discord or forums, writeups for public boxes). You can't know to look for something that you don't know exists.
I think that's it! There are some tools and other things that I could recommend, but this post is way too long as it is. I'll do a couple more posts with more detail if there's interest. Thanks for reading.
